
Recently I have found a vulnerability inside Cisco’s Packet Tracer product which allows an attacker to traverse and access local files by exploiting the file:// scheme inside an iframe that can be embedded in activity wizard’s instruction window which is launched on start.
Affected versions
- All versions prior to 8.2.1
The discovery
While playing around with javascript inside the Instructions tab for Activity wizard I started thinking about ways to escape the webengine, trying to fetch with the file:// scheme was the first idea, but oddly when I tried to make a http request I couldn’t access the response, I knew for a fact that it had access to the internet as I had used an iframe earlier, perhaps my code was wrong but trying to debug such wasn’t easy, there’s no console and the javascript code kept running a loop so using alert() was very annoying. Instead I tried another way to make http requests, using iframes, as I earlier mentioned those worked. I used file://g:/secret.txt as the source and voila
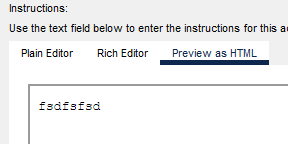
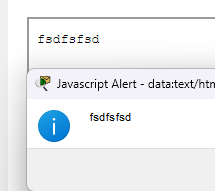
Is this actually useful though? Can I read iframe content with javascript? Sure I can, I made a simple script that would run on page load and try to read the contents of my iframe with the id “test”
<script>
window.addEventListener("load", (event) => {
alert(document.getElementById('test').contentWindow.document.body.innerText);
});
</script>
<iframe id="test" src="file://G:/secret.txt"/>
The implications
A bad actor could publish a malicious packet tracer activity that would read common sensitive files and send those to a remote server
A malicious student could infect an already existing packet tracer activity[1] that would normally be sent back to the lector and opened for a review.
[1] A packet tracer activity while encrypted can still be decrypted with enough reverse engineering knowledge, thus being able to modify the activity wizard password and encrypt it back to its original form.
Timeline
2022-12-07T23:00:00Z : Vulnerability discovered
2022-12-09T10:38:00Z : A bug report was sent to the PSIRT
2022-12-12T23:19:00Z : A bug case was opened by the PSIRT and I received a reply
2023-03-13T23:00:00Z: Cisco Packet Tracer 8.2.1 was released fixing the vulnerability